Finest Data Security Services for Businesses
pA Cybersecurity report sponsored by Herjavec Group showed that cybercrime damages are expected to hit 6 trillion per year by 2021 Cybercrime is changing consumers behavior online and it causes customerbusiness distrust organizationwide security issu
More businesses are storing their customers' data online and this has increased their vulnerability to cyber-attacks increasing the need to deal with online criminals and this has significantly increased cybersecurity costs which may eventually be transferred to consumers.
A Cybersecurity report sponsored by Herjavec Group showed that cybercrime damages are expected to hit $6 trillion per year by 2021. Cybercrime is changing consumers' behavior online, and it causes customer-business distrust, organization-wide security issues, and concerns for all B2B operations.
Many businesses do not invest in cybersecurity either because they don't feel the need or because they feel helpless in the face of such a massive threat, while in reality, there are many things businesses can do to stop cybercriminals from harming their operations.
This article will help you learn more about the effects of cybercrime on businesses and the best data security services available to help you overcome the challenges posed by cybercrime so that you can determine the best ways to prevent your company from becoming a victim.
Finest Data Security Services for Businesses
Data discovery and classification
The best way to protect your data effectively requires one to know exactly what sensitive information they have. Data discovery and classification solutions will scan your data repositories for the types of data you consider important, based on various industry standards or your custom requirements, sort it into different categories, and clearly label it with a digital signature indicating its classification.
Businesses can use those labels to focus your information security resources and execute controls that protect data in accordance with its value to the organization. If data is altered, its classification can be updated.
Firewall
A firewall is usually one of the first lines of defense for a network because it isolates one network from another. They exclude unacceptable traffic from entering the network. Additionally, you can open only limited ports, which gives hackers less room to maneuver to get in or download your sensitive data.
The firewall might completely disallow some or all traffic, depending on the organization's firewall policy or it might perform verification on some or all of the traffic.
Backup and recovery
A backup and recovery solutions helps companies protect themselves in case data is lost or corrupted. All important business assets should be duplicated periodically to provide redundancy in case of a server failure, accidental deletion, or malicious damage from ransomware or other attacks. This will allow you to restore your data quickly.
Antivirus
Antivirus solutions are one of the most widely adopted security tools for both personal and commercial purposes. There is a large number of antivirus software vendors in the market, but they all use pretty much the same techniques to detect malicious code. Antivirus solutions help to detect and remove malicious programs that may affect the integrity of your data.
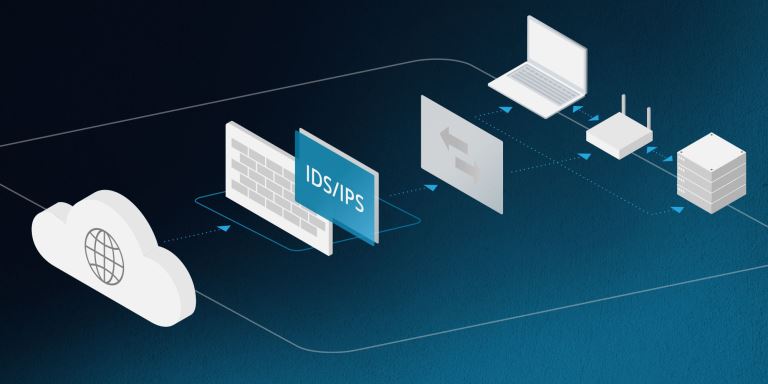
Intrusion detection and prevention systems(IDPS)
An IDPS is one of the more critical devices in any organization's overall security strategy. There is too much data for any human analyst to inspect for evidence of intrusions. The IDPS helps alert humans to such events to investigate, and prioritize correction. It also serves an important auditing function.
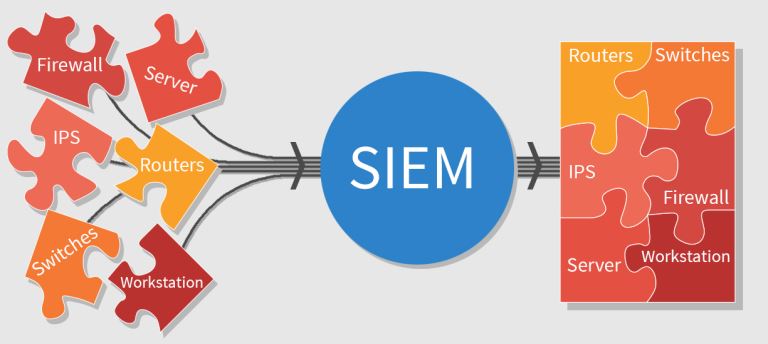
Security information and event management(SIEM)
SIEM solutions provide real-time analysis of security logs that are recorded by network devices, servers and software applications. They aggregate and correlate the events that come in, and also perform event deduplication: removing multiple reports on the same instance and then act based on alert and trigger criteria.
It also usually provides an analytics toolkit that helps companies find events that you currently need such as events related to data security. They also help businesses in data security investigations in case of a breach.
Data loss prevention
Data loss prevention systems monitor systems and networks to make sure that sensitive data is not altered, copied or deleted. They also monitor who is using and transmitting data to detect unauthorized use. It helps in minimizing the risk of unauthorized access to systems forming a foundational part of information, data, and network security.
Access control
Access control is a method of restricting access of sensitive data to only users that have had their identity verified and allowed access through an access control gateway.
This ensures that unauthorized users cannot get access to a business' or client's information
Cloud security solutions
Cloud computing is the delivery of hosted services, including software, hardware, and storage, over the Internet therefore cloud security refers to the technologies, policies, controls, and services that protect cloud data, applications, and infrastructure from threats.
This service helps businesses in managing users and their access privileges (identity and access management), the safeguarding of cloud accounts from unauthorized access, the encryption and protection of cloud-based data assets, and managing its security posture (compliance).
Auditing
A security audit aids you to find whether there is any number of cybersecurity challenges and risks to your business and technological operations. Once you are armed with the IT audit report, you can find the right cybersecurity services company that can assess your company's security strengths and loopholes concerning them.
Data encryption
Encryption works to encode your data so that it cannot be read without a password. It surrounds your data with a robust layer of security – more than what simple password protection could ever offer. This is essential to many different organizations, especially those that are regulated by HIPAA, GLBA, or FNRA.
Businesses can encrypt file-by-file on an as-needed basis to protect sensitive data, especially when sending files over an unsecured wired or wireless network, you can unknowingly be exposing your sensitive data to thieves. Encryption provides an extra layer of security on both secured and unsecured networks.
Biggest Cyber-threats businesses face
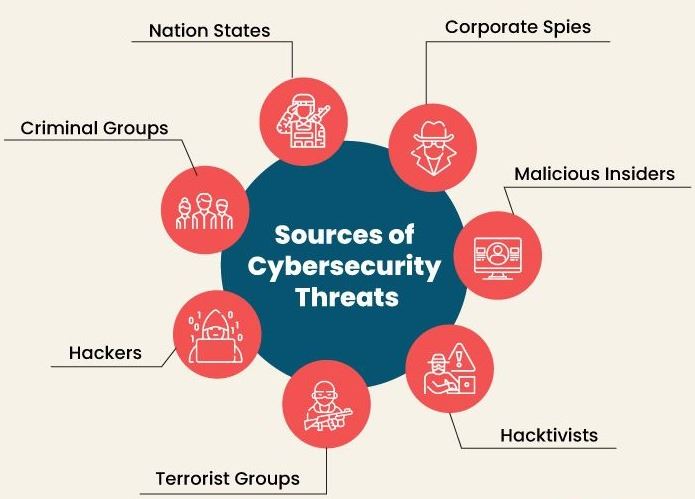
A cyber security threat can be defined as any possible malicious attack that seeks to unlawfully access data, disrupt digital operations or damage information. Cyber threats can originate from different actors, including corporate spies, hacktivists, terrorist groups, hostile nation-states, criminal organizations, lone hackers and disgruntled employees.
In recent years, numerous high-profile cyber-attacks have resulted in sensitive data being exposed. For example, the 2017 Equifax breach compromised the personal data of roughly 143 million consumers, and in 2018, Marriott International disclosed that hackers accessed its servers and stole the data of roughly 500 million customers. In both cases, the security threat was enabled by the organization's failure to implement, test and retest technical safeguards, such as encryption, authentication and firewalls.
Below is a list of the most common cyber-threats that many businesses face;
- Denial of service
- Phishing attacks
- Malware attacks
- Ransomware
- Weak passwords
- Insider threats
- Weak cyber-security policies and procedures
Impact of cyber-attacks on your business
Successful cyber-attacks cause major damage to businesses affecting the company's bottom line, as well as your business' reputation and consumer trust. The impact of such a breach can be divided into three broad categories: financial, reputational, and legal.
- The financial cost of a cyber-attack
According to a survey by InsuaranceBee, 83% of SMEs are not financially to recover from a cyber-attack while a study by Accenture found that 43% of data breaches occur at SMEs.
Cyber-attacks generally result in a substantial financial loss arising from:
- Theft of corporate information
- Theft of financial information (e.g. bank details or payment card details)
- Theft of money
- Disruption to trading and operations (e.g. ability to carry out transactions online is hindered)
- Loss of business or contract
Businesses that suffered a cyber-breach also incurred costs that are associated with repairing the affected systems.
- Reputational damage
Cyber-attacks can damage the reputation of your company causing an erosion of trust. This can lead to:
- Loss of customers
- Loss of sales
- Reduction in profits
The damage on your business' reputation can impact relationships between suppliers, partners or even investors and other 3rd parties vested in your business.
- Legal consequences of a cyber-breach
Data protection and privacy laws requires businesses to manage the integrity of all personal data you hold. Accidental or deliberate compromise of this data may lead to you facing large fines and regulatory sanctions.
How can you minimize the impact of cyber-attacks on your business?
Security breaches can devastate even the largest businesses in the world. This makes it extremely important to manage the risks by having an effective cyber security incident response in case an attack happens. This would help you to;
- Reduce the impact of the attack
- Report the incident to the relevant authority so as to clean up the affected systems
- Get your business up and running
Conclusion
Traditionally, cybersecurity was always seen as an IT issue, but with the recent advancement in technology, it is taking center stage as a business issue that should be taken seriously. It is critical for businesses both large and small to put in place solutions that protect data and personal information to reduce disruptions from cyber-threats.
Did you find this article helpful? Kindly visit our consultation services for more articles like this.