What are the Best Practices for SQL Server Manager
To succeed in SQL server management, you must know everything about its best practices. If you don't know yet, this article is for you. It's informative enough to help you learn as much as you can about the best practices for SQL server managers.
There are several best practices for SQL server managers, such as; avoiding index fragmentation, ensuring data lineage and integrity, using a local SSD to improve IOPS, optimizing virtual log files, auditing and reporting, and row-level protection.
Keep reading to learn more about the common challenges associated with SQL server management.
What are the Best Practices for SQL Server Manager
Whether using Microsoft SQL Server or the open-source MySQL database, you must ensure that your security procedures are solid and reliable. This is crucial for avoiding unwanted access to your database, mainly if you keep sensitive or private data on your servers. You may put various SQL Server security best practices into practice to safeguard your database and keep up with compliance requirements as necessary.
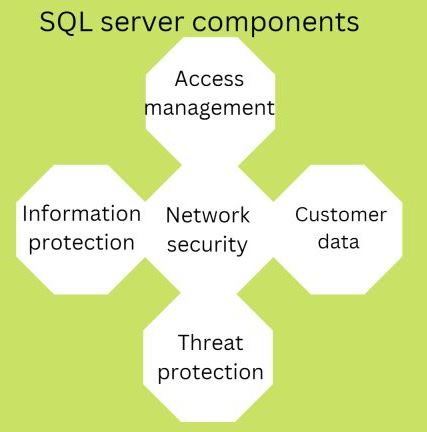
What are the components of an SQL server?
For an easier understanding of the components of the SQL server, check the chart below;
What are SQL server best practices?
1. Row-Level Protection
Row-Level Security (RLS) allows user execution context to limit access to specific rows in a database table. Users can only see the records that are relevant to them, thanks to RLS. Without needing to make significant changes to your program, this provides "record level" security. The security policy toggles the RLS capability on and off and contains the business logic within table-valued functions. Additionally, the FILTER and BLOCK predicates, connected to the RLS tables, are governed by the security policy. To restrict the records returned to the user making the call, employ Row-Level Security (RLS).
2. Optimizing Virtual Log Files
Track the expansion of the virtual log file and take appropriate steps to avoid log file fragmentation. You can create segments of virtual log files from the Physical Transaction Log File (VLF). When the physical transaction log file needs to grow, new VLFs are generated. If auto-growing was left enabled and growth occurred too frequently, it would produce many VLFs. Log file fragmentation, which is analogous to disk fragmentation and can harm performance, can result from this behavior.
3. Auditing and Reporting
Create an audit policy for auditing the SQL server or database level. All databases on the server, both old and new, are subject to server policies. Enable server-level auditing and permit database-level auditing to take the server-level property into account for all databases. Check the tables and columns with critical information and security controls in place. An assumption is that a table or column is vital enough to warrant auditing if it requires security capability protection. You should not audit or review often tables with sensitive information if you cannot apply security controls due to application or architectural limitations.
4. Avoid Index Fragmentation
Defragment your most frequently updated tables' indexes regularly. Your tables' indexes may become fragmented, which could cause queries that use these indexes to execute poorly. Rearranging the indexes on your most frequently updated tables should be a routine maintenance task.
5. Ensure Data Lineage And Data Integrity
It can be helpful to have historical records of those changes to address unintentional changes to the data. When a lousy actor introduces unlawful data changes, it can also benefit application-change auditing and enable data items' recovery. Temporal tables can store record versions through time and observe data as it has changed throughout a record's existence—this aids in providing a historical perspective of the data in your application. Thus you can use temporal tables to give a copy of the current table at any moment.
6. Use a Local SSD To Improve IOPS
For housing the tempdb and Windows paging files, create fresh instances of SQL Server with one or more local SSDs. The transitory nature of local SSD technology makes it unsuitable for use with your crucial databases and information. The Windows paging and tempdb are both temporary files, making them excellent candidates to be moved to a local SSD-this transfer a sizable amount of I/O operations away from your SSD persistent disks. See Setting up TempDB for details on how to do this.
What are the Common Challenges Facing SQL Server?
If you write queries and work in SQL frequently, there's a strong chance you've encountered a variety of performance threats. You could be experiencing memory problems, slow-running or poorly written queries, inefficient subqueries, indexes with a lot of writes but few or no reads, or indexes with a lot of writes but few or no reads. Below are the common threats facing SQL Server.
1. Locking Contention
Locking contention can happen when multiple processes attempt to update locks simultaneously on the same lock resources. Additionally, a deadlock can occur when two or more jobs prevent one another from completing because they each have a lock on a resource that the other processes seek to lock. You can interpret this as numerous requests coming from various users for server-side functions. Due to many processes being able to seek access to the same database resources at once, conflicts are more likely to arise over time.
2. No Encryption Or Poor Encryption
If your database or the information included is not encrypted, hackers can locate the connection points between the system and the network and breach the database. Therefore, DBAs must retain the SQL database or the data within the database in encrypted form to prevent such situations. It works with both the primary database and the backup files.
3. Missing Security Updates And Patches
For databases lacking security updates or using outdated SQL Server versions, malware attacks remain a constant concern. If DBAs neglect to apply the most recent security patches to SQL Server, the server is susceptible to malware attacks.
4. Bad Indexes
The underlying indexes may be degrading overall performance if a table's and its indexes' write functions are significantly more frequent than their read functions. A corresponding adjustment must be activated to the column indexes whenever a write operation occurs to a SQL column with an index. If most of the activity is a writing activity, it would be worthwhile to consider deleting or changing the relevant indexes. So doing this would probably improve performance by lowering the total output of writing activity.
What are the Causes of Memory Problems in SQL Server.
Memory problems are among the common challenges in SQL. Servers typically consume a lot of memory, even if the server has a lot of installed RAM. Data is automatically stored in memory caches by SQL Server to increase performance and use less memory. Unless SQL needs to update the data, data that has been read from the drive won't alter once it has been read.
The table below shows the common causes of Memory Problems in SQL
| Cause | Explanation |
|
Internal memory pressure |
Low memory availability resulting from causes within the SQL Server process is called internal memory pressure. |
| OS or external memory pressure from the SQL server | An external force causes insufficient memory for SQL Server, high memory use from a component outside the process. |
| Internal memory pressure from the SQL server | Out-of-memory errors can also be caused by internal memory strain brought on by parts of the SQL Server engine. Memory clerks track numerous features that allocate memory in SQL Server. |
Conclusion
Enterprise-class database platform SQL Server is expanding. Many businesses use it since it is widely known. This indicates that hackers are increasingly attacking SQL Servers. You expose them to data breaches and stolen information if your SQL server access isn't secure. Although managing SQL Server security can be one of the trickiest things you have to do, it's also one of the most important. Keeping your servers isolated, enforcing rights, optimizing virtual log files, installing antivirus software, etc. You can reach out to Guru Solutions for quality SQL Server Management services.