Strengthen your defenses with Guru Solutions' expert cybersecurity audit and security assessment services. We identify weaknesses through vulnerability assessment and penetration testing, enhance risk management, and ensure compliance audit readiness. Protect your business today.
Get Started



Fortify Your Defenses Today
Take Control of Your Cybersecurity Posture
Guru Solutions' expert cybersecurity audit services provide the clarity and insights you need to proactively protect your business and digital assets. Our thorough assessment identifies weaknesses before attackers can exploit them, giving you the upper hand in the fight against cybercrime.
Investing in a professional security assessment is investing in the future resilience of your organization. Guru Solutions delivers a comprehensive evaluation of your defenses, pinpointing critical vulnerabilities and providing a clear roadmap for improvement.
Ready to get a true picture of your security landscape? Guru Solutions offers detailed vulnerability assessment and penetration testing to uncover hidden risks. Let our certified professionals simulate real-world attacks in a controlled environment to reveal exploitable paths and help you build a stronger, more secure foundation for your business's success in the digital age.
Understanding the Need for a Proactive Cybersecurity Audit
In an era where digital transformation is accelerating business operations, the threat landscape is expanding at an alarming rate. Organizations are increasingly reliant on complex IT infrastructures, cloud services, and interconnected systems, each presenting potential entry points for malicious actors. A reactive approach to cybersecurity, only addressing issues after an incident occurs, is no longer sustainable or responsible.
The financial, reputational, and operational consequences of a successful cyberattack can be devastating, often leading to significant recovery costs, legal liabilities, and a loss of customer confidence that can take years to rebuild. Therefore, a proactive strategy centered around regular and thorough cybersecurity audits is absolutely essential for identifying potential weaknesses before they can be exploited by adversaries seeking unauthorized access or disruption.
A comprehensive cybersecurity audit serves as a vital health check for your organization's digital security posture. It systematically evaluates the effectiveness of your existing security controls, policies, and procedures against established industry standards and best practices. This rigorous process helps uncover hidden vulnerabilities within your network, applications, and physical security layers that automated tools alone might miss.
By gaining a deep understanding of your security gaps, you can prioritize remediation efforts, allocate resources effectively, and implement targeted defenses that significantly reduce your exposure to potential threats. Such an audit provides not just a snapshot of your current security state but also a clear roadmap for continuous improvement, ensuring your defenses evolve as quickly as the threats themselves.
Furthermore, regular cybersecurity audits are often a prerequisite for achieving and maintaining compliance with various industry regulations and data protection mandates, such as GDPR, HIPAA, PCI DSS, and others. Demonstrating due diligence through independent security assessments helps satisfy regulatory requirements and builds trust with customers and partners who entrust you with sensitive data.
Beyond compliance, a strong security posture is a competitive advantage, signaling to the market that you take the protection of information seriously. Guru Solutions specializes in conducting these essential audits, providing the expertise and insights necessary to navigate the complexities of modern cybersecurity and build a resilient defense that safeguards your business against an ever-present array of sophisticated digital threats.
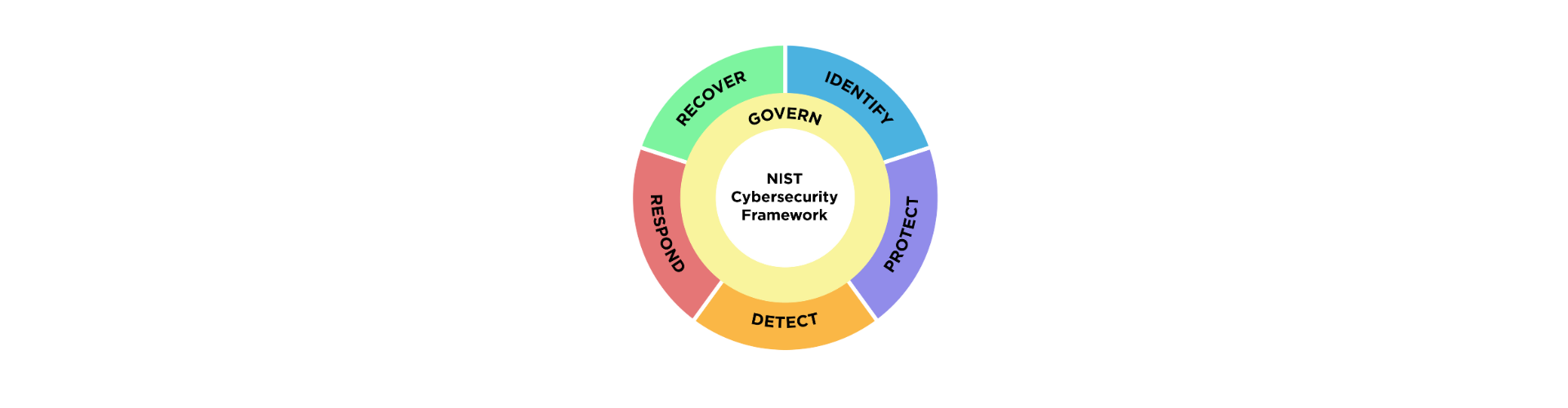
NIST Cybersecurity Framework
Guru Solutions structures its comprehensive cybersecurity audit services around robust, globally recognized frameworks, prominently utilizing the NIST Cybersecurity Framework. This adaptable framework provides a standardized and systematic approach to evaluating your organization's security posture across five key functions: Identify, Protect, Detect, Respond, and Recover. Our deep expertise in applying the NIST CSF allows us to methodically assess your current security controls, pinpoint gaps, and provide a clear, organized view of your risk landscape relative to established best practices, demonstrating our capability to implement structured methodologies that deliver consistent, high-quality security assessments aligned with international standards for managing and reducing cybersecurity risks effectively.

Vulnerability Scanning Tools
A cornerstone of our security assessment process involves the strategic use of advanced Vulnerability Scanning Tools. These sophisticated software platforms are essential for automatically identifying known security weaknesses in networks, servers, applications, and other digital assets by comparing configurations and software versions against extensive databases of known vulnerabilities. However, our expertise extends far beyond merely running automated scans; our certified analysts possess the critical skill to interpret the results, differentiate between genuine threats and false positives, correlate findings from various sources, and prioritize vulnerabilities based on their actual risk and potential impact on your specific environment, showcasing our ability to transform raw scan data into actionable intelligence for a more effective vulnerability assessment.

Network Traffic Analysis Tools
Understanding the flow of data within your network is crucial for identifying potential security threats and policy violations, which is why Guru Solutions expertly utilizes Network Traffic Analysis Tools. Tools such as Wireshark enable our team to capture and perform deep-packet inspection, meticulously analyzing the data traversing your network infrastructure. This granular level of analysis allows us to gain profound insights into communication patterns, identify unusual or potentially malicious traffic indicative of compromise attempts, and uncover insecure configurations or protocols that could be exploited. Our proficiency in dissecting network traffic demonstrates a high level of technical skill, enabling us to reveal subtle security issues and gain a comprehensive understanding of your network's true security state, complementing our other assessment activities effectively.

Penetration Testing Methodologies
When performing simulated attacks as part of our cybersecurity audit services, Guru Solutions strictly adheres to established and respected Penetration Testing Methodologies, including frameworks like OSSTMM and PTES. These methodologies provide a detailed, ethical, and repeatable process for planning, executing, and reporting on controlled attempts to exploit identified vulnerabilities to gain unauthorized access to systems or data. Our commitment to following these rigorous standards ensures that our penetration tests are conducted professionally, safely, and effectively, providing realistic insights into your organization's resilience against real-world threats. Our expertise in applying these methodologies allows us to demonstrate the practical exploitability of vulnerabilities, providing tangible proof of concept and revealing attack paths, thereby significantly enhancing the value of our security assessment by simulating genuine threat scenarios responsibly.
How Guru Solutions Conducts Your Security Assessment
Guru Solutions approaches each security assessment with a meticulous, multi-layered methodology designed to provide a comprehensive view of your organization's defenses. We begin by collaborating closely with your stakeholders to fully understand your business processes, critical assets, and unique risk profile. This initial phase is crucial for tailoring the audit scope to ensure it aligns perfectly with your specific needs and compliance obligations.
Our experienced team then employs a combination of automated scanning tools and manual techniques to perform detailed reconnaissance, mapping your network infrastructure and identifying potential areas of interest for deeper investigation. This dual approach ensures that we capture a wide range of potential vulnerabilities, from common misconfigurations to complex logic flaws that only expert manual analysis can uncover effectively, establishing a strong foundation for the subsequent phases of our assessment process.
Following the information gathering, our experts delve into the vulnerability assessment phase, systematically scanning your systems, applications, and network devices for known weaknesses. We utilize industry-leading tools and proprietary techniques to identify vulnerabilities based on extensive databases of known security flaws and misconfigurations. Each identified vulnerability is then analyzed to determine its potential impact and likelihood of exploitation, allowing us to prioritize findings based on the risk they pose to your organization.
This detailed analysis goes beyond simply listing vulnerabilities; we provide context, explain the potential consequences of each finding, and offer initial recommendations for mitigation, empowering you with the knowledge needed to make informed decisions about strengthening your defenses effectively against potential threats and improving your overall security posture significantly.
Depending on the agreed scope, Guru Solutions may also conduct penetration testing to simulate real-world attack scenarios. Our certified ethical hackers attempt to safely exploit identified vulnerabilities to gain unauthorized access, demonstrating the pathways an attacker might take and the potential impact on your critical systems and data. This hands-on testing validates the findings from the vulnerability assessment and provides tangible proof of concept, highlighting the effectiveness of your existing security controls and identifying areas where additional layers of defense are required.
The insights gained from both the assessment and testing phases are compiled into a comprehensive report, providing a clear and actionable roadmap for enhancing your security posture, managing risks effectively, and bolstering your defenses against the evolving landscape of cyber threats with confidence and strategic insight.
"In today's digital economy, understanding your security posture is not a luxury, but a fundamental necessity. Our Cybersecurity Audit Services provide the critical clarity businesses need to navigate the threat landscape with confidence and resilience."
Get Your Security Assessment
Ready to fortify your digital defenses? Contact Guru Solutions today to schedule your comprehensive cybersecurity audit. Our team will work with you to understand your unique needs and provide a tailored assessment plan.

Achieving Compliance and Enhancing Risk Management
Beyond identifying technical vulnerabilities, a critical component of Guru Solutions' cybersecurity audit services is assisting your organization in meeting its regulatory and compliance obligations. Numerous industries are subject to strict data protection laws and standards, such as GDPR, HIPAA, PCI DSS, SOC 2, and ISO 27001. Failing to comply with these mandates can result in significant fines, legal action, and damage to your reputation.
Our audits are designed to evaluate your security controls against the specific requirements of the regulations relevant to your business, providing a clear picture of your current compliance posture and highlighting any gaps that need to be addressed to meet mandatory legal and industry benchmarks effectively and responsibly.
Integrating risk management into your overall security strategy is paramount, and our security assessment services play a vital role in this process. We don't just report on technical findings; we help you understand the potential business impact of each identified vulnerability and risk. By assessing the likelihood of exploitation and the potential consequences, we help you prioritize remediation efforts based on genuine risk levels.
This allows you to allocate resources wisely, focusing on addressing the threats that pose the greatest danger to your operations, data, and reputation. Our reporting includes a clear risk matrix, enabling your leadership team to make informed decisions about managing cyber risks effectively and strategically within the context of your broader business objectives and operational constraints.
Furthermore, the insights gained from a Guru Solutions cybersecurity audit contribute significantly to the continuous improvement of your information security management system (ISMS). By providing a baseline assessment and identifying areas for enhancement, the audit report serves as a valuable tool for refining your security policies, procedures, and technical controls.
Regular audits help demonstrate due diligence to auditors, regulators, and stakeholders, building confidence in your commitment to protecting sensitive information. Partnering with us helps you move from a reactive stance to a proactive, risk-aware security culture, ensuring your defenses are not static but continuously evolving to meet the challenges of the dynamic cyber threat landscape effectively and sustainably over the long term.
Cause
- Increasingly sophisticated cyberattacks targeting businesses of all sizes.
- Compliance requirements from industry regulations (e.g., GDPR, HIPAA, PCI DSS).
- Lack of visibility into the current state of your IT infrastructure's security.
- Recent changes to your network, systems, or software that may introduce new vulnerabilities.
Benefits
- Identify and mitigate vulnerabilities before they can be exploited by attackers.
- Improve overall security posture and resilience against cyber threats.
- Ensure compliance with relevant industry standards and legal regulations.
- Enhance your organization's risk management framework and decision-making.
FAQ
The duration of a cybersecurity audit can vary significantly depending on the size and complexity of your IT infrastructure, the scope of the audit defined during the initial planning phase, and the specific services included, such as in-depth vulnerability assessment or comprehensive penetration testing. A smaller scope audit might take a few days, while a large enterprise-wide assessment could take several weeks. Guru Solutions works closely with you to establish a realistic timeline during the scoping phase, ensuring minimal disruption to your operations while delivering a thorough and effective security evaluation tailored to your specific needs and environmental considerations.
Upon completion of the technical assessment phases, Guru Solutions delivers a detailed report outlining all findings from the security assessment. This report includes an executive summary, a list of identified vulnerabilities prioritized by risk, evidence of findings (including potential exploitation during penetration testing), and actionable recommendations for remediation. Our team will then walk you through the report, explaining the findings and providing expert guidance on implementing the necessary security enhancements. We are available to answer questions and offer ongoing support as you work to strengthen your defenses and address the identified risks effectively, ensuring the insights from the audit translate into tangible security improvements for your organization.
While often related and sometimes included within the scope of an audit, cybersecurity audit and penetration testing are distinct but complementary services. A cybersecurity audit is a broader security assessment that evaluates your overall security posture, including policies, procedures, and technical controls, against established standards and best practices. Vulnerability assessment is typically part of this audit, identifying potential weaknesses. Penetration testing, on the other hand, is a more focused activity where certified ethical hackers attempt to actively exploit identified vulnerabilities in a controlled environment to simulate a real-world attack and demonstrate the potential impact of a breach, providing tangible proof of exploitability and the effectiveness of existing defenses. Guru Solutions offers both services, tailoring the approach to meet your specific security objectives and provide the most comprehensive evaluation possible.
Testimonial



Secure Your Business Now
Ready to strengthen your defenses with a professional cybersecurity audit? Contact Guru Solutions to discuss your specific needs and get started on the path to a more secure future.
How to Get it Done
We have a team of experts to help customize your software. Guru Solutions also offers a consultation service if you need advice on the software to use. We offer the best services at fair prices. Give us a call to schedule a meeting; invite us to your office or even home, and we will be there.



